
To ensure compliance and data protection when working with IT firms in Melbourne, put APP- and NDB-aligned contracts and DPAs in place, run structured vendor risk assessments, enforce and validate technical controls, govern cross-border data, select relevant assurance frameworks, agree a joint incident response playbook, mandate residency/retention/deletion policies, avoid common procurement pitfalls, and continuously test and monitor ideally orchestrated end-to-end in AWD.
Context and background: why Melbourne buyers must operationalise privacy and security, not just document it
Melbourne organisations operate under the Australian Privacy Act 1988 (Cth) and the Australian Privacy Principles (APPs), with the Notifiable Data Breaches (NDB) scheme requiring “eligible data breach” assessment within 30 days and notification “as soon as practicable” if likely to cause serious harm. APP 11 requires reasonable steps to protect personal information; APP 8 governs cross-border disclosures. For regulated sectors (APRA CPS 234, Victorian public sector under VPDSF), expectations are higher and more prescriptive. In this environment, outsourcing to an IT firm does not outsource accountability your organisation remains responsible.
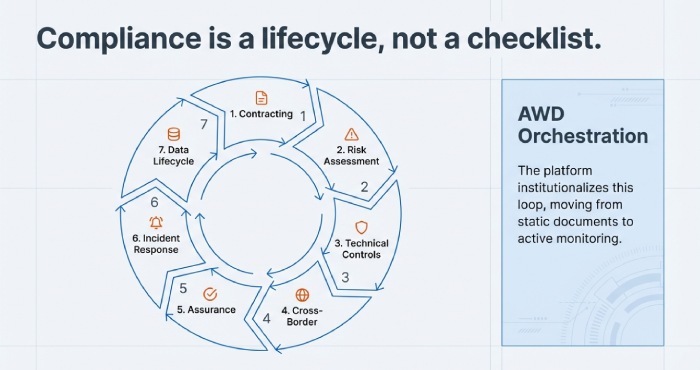
Compliance is a lifecycle, not a checklist. It begins with vendor selection and contracting, continues through design reviews and control validation, and relies on ongoing monitoring, evidence collection, phishing risk mitigation, and incident readiness. AWD, a compliance orchestration platform, helps Melbourne buyers institutionalise this lifecycle by standardising clauses mapped to the APPs, automating vendor assessments, collecting technical evidence, tracking assurance frameworks, and running incident playbooks with audit-ready records—including preparedness for phishing-related incidents.
Below is a practical, Melbourne specific blueprint contract templates, risk models, controls, cross-border mechanisms, assurance priorities, incident coordination, data lifecycle policies, and role-based checklists each tied explicitly to how AWD accelerates and evidences your compliance program.
Contracts and DPAs: clauses that satisfy the Privacy Act 1988 and NDB scheme
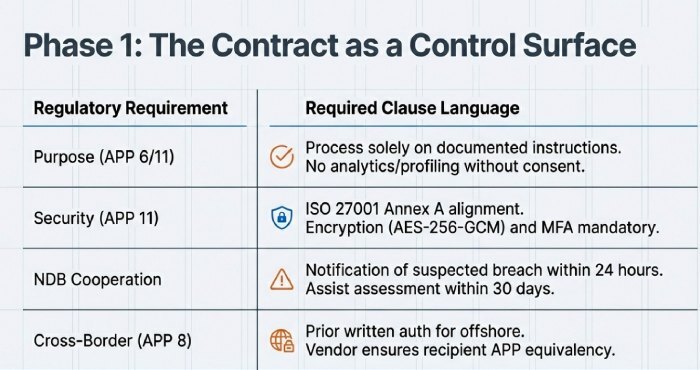
A strong contract is your first control surface. Require a Master Services Agreement (MSA) + Data Processing Agreement (DPA) with clauses tied to APPs and NDB.
Must-have clauses and sample language
- Purpose and instructions (APP 6, APP 11)
“Supplier will Process Personal Information solely on documented instructions from Customer for the purposes described in Schedule 1; any use for analytics, profiling, or product improvement requires Customer’s prior written consent.” - Security measures (APP 11)
“Supplier will implement and maintain administrative, technical, and physical safeguards no less stringent than ISO/IEC 27001 Annex A controls, including encryption at rest (AES-256-GCM), in transit (TLS 1.3), MFA for privileged access, and 12-month log retention.” - Notifiable Data Breaches (NDB) cooperation
“Supplier will notify Customer within 24 hours of becoming aware of an Incident reasonably suspected to be an Eligible Data Breach, and will assist with investigation and assessment under the NDB scheme within the 30-day statutory timeframe.” - Cross-border disclosures (APP 8)
“Supplier will not disclose Personal Information outside Australia without Customer’s prior written authorisation and only where Supplier ensures the overseas recipient is bound by contractual obligations substantially similar to the APPs; Supplier remains liable for the recipient’s non-compliance.” - Subprocessors
“Supplier must obtain Customer’s prior written consent to engage Subprocessors and will flow down obligations equivalent to this DPA; Supplier remains fully liable for Subprocessor acts and omissions.” - Audit and evidence
“On 30 days’ notice, and immediately post-Incident, Customer may audit Supplier’s compliance, including review of SOC 2/ISO 27001 certificates, penetration test summaries, and control evidence; Supplier will remediate material findings within agreed SLAs.” - Breach costs and liability
“Supplier will bear reasonable costs of Incident response, forensics, and notification caused by Supplier’s breach of this Agreement. Supplier will maintain cyber liability insurance of at least AUD $5M aggregate.” - Termination, return, and deletion (NIST 800-88)
“Within 30 days of termination, Supplier will return all Personal Information and will securely erase all copies in accordance with NIST SP 800-88 Rev. 1; Supplier will provide a deletion certificate.” - Assistance and complaints (APP 1, APP 12/13)
“Supplier will assist with OAIC inquiries, data subject access/correction requests, and privacy impact assessments at no additional charge.”
Vendor security and privacy risk assessments: templates, scoring, and cadence
Vendor risk must be right-sized and repeatable.
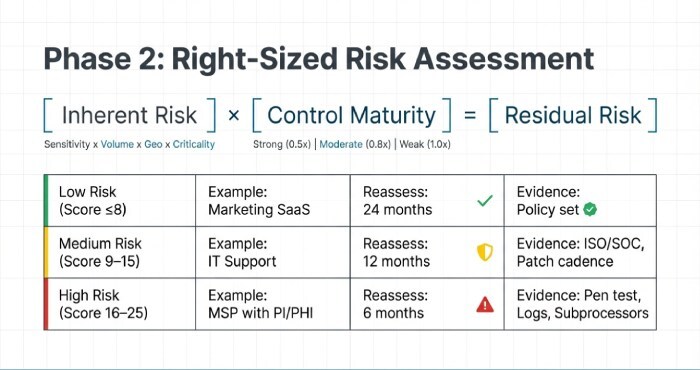
Risk tiering model
- Inherent risk score (1–25): Data sensitivity (1–5) × Volume (1–5) × Connectivity (1–5) × Geography (1–5) × Criticality (1–5).
- Residual risk score (1–25): Inherent risk adjusted by control maturity (0.5× for strong, 0.8× for moderate, 1× for weak).
Due diligence steps
- Pre-award: Security questionnaire (CAIQ-Lite or AWD 120-control set), policy reviews, external posture scan, reference checks, and certifications (ISO 27001, SOC 2).
- Technical validation: Evidence of encryption, IAM configuration, logging coverage, patch/vulnerability management cadence, backup/restore tests.
- Legal/privacy: DPA and cross-border disclosures, data map, privacy policy alignment, DPIA/PIA where high risk.
- Ongoing monitoring: Quarterly KPI/OKR reviews, annual reassessment, material change notifications.
Recommended frequency and evidence by tier
| Risk Tier | Examples | Reassess | Evidence Required |
| Low (≤8) | Non-PII tools, marketing SaaS | 24 months | Policy set, SOC report if available |
| Medium (9–15) | IT support with limited PI | 12 months | ISO/SOC, patch cadence, backup test, incident summary |
| High (16–25) | Managed service provider with PI/PHI | 6 months | Pen test summary, access reviews, log samples, DR test results, subprocessor list |
Technical controls to implement and validate for Melbourne IT suppliers
The Privacy Act’s “reasonable steps” standard maps to concrete, testable controls.
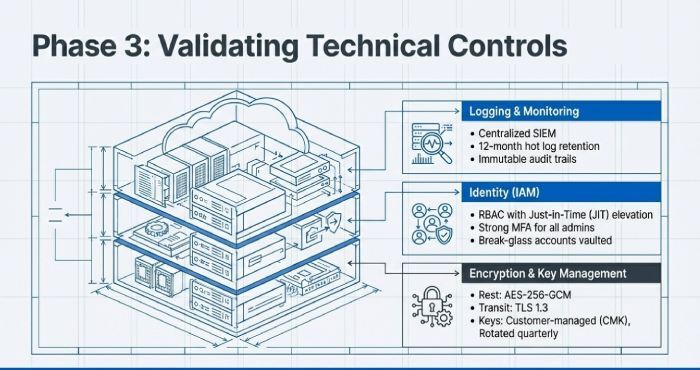
Encryption and key management
- Algorithms: AES-256-GCM for data at rest; TLS 1.2 (prefer 1.3) for transit; RSA-3072 or ECDSA P-256 for certificates.
- Key management: Customer-managed keys (CMK) in HSMs or KMS (segregated per environment), quarterly key rotation (crypto-period ≤12 months for DEKs; ≤24 months for KEKs), dual control for key access, and audit trails.
- Validation: Provide KMS policy screenshots, key rotation logs, TLS test results, and architecture diagrams. AWD collects and time-stamps this evidence, alerting on stale keys and weak cipher suites.
Access control and identity
- Models: RBAC or ABAC, least privilege, just-in-time (JIT) elevation, strong MFA for all admins, passwordless/FIDO2 recommended.
- Privileged access: Break-glass accounts vaulted and monitored; quarterly privilege reviews; session recording for admin consoles.
- Joiner-Mover-Leaver: 24-hour deprovisioning SLA.
Logging, monitoring, and vulnerability management
- Logging: Centralised SIEM; capture admin actions, authentication events, data access, network flows; retain ≥12 months hot logs.
- Detection: Mapped to MITRE ATT&CK; alert SLAs defined; EDR on servers/endpoints; anti-malware with cloud detonation.
- Vulnerabilities: Weekly scans; priority patch windows (Critical ≤7 days; High ≤14 days); risk exceptions with expiry.
Data minimisation and segregation
- Environment separation: Dev/Test/Prod isolated; no PI in lower environments; synthetic data where possible.
- Data lifecycle: Collection limited to purpose; automatic purging based on retention schedules; tokenisation for high-risk fields.
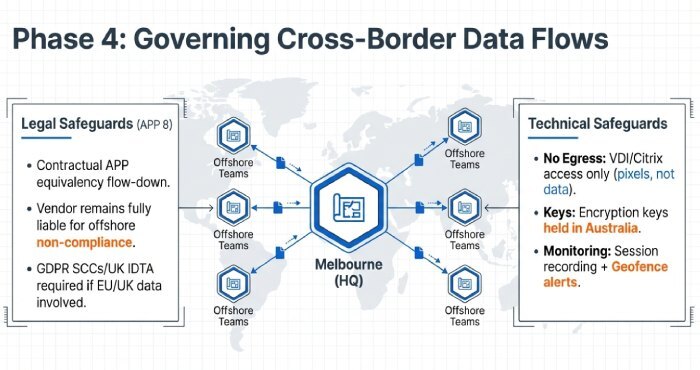
Cross-border data flows with offshore subcontractors: legal and technical safeguards
Melbourne IT firms may leverage offshore teams. Under APP 8, you must take reasonable steps to ensure overseas recipients don’t breach the APPs.
Legal mechanisms
- Contractual APP equivalency: Flow-down clauses obligating APP-equivalent protections; vendor remains liable for offshore parties.
- Informed consent: Obtain explicit consent from individuals where feasible and appropriate.
- Localisation preference: Require Australian data residency unless specifically authorised.
If EU/UK personal data is processed, require GDPR SCCs/UK IDTA. For APRA-regulated entities, align with CPS 234’s third-party obligations and notification to APRA for material incidents.
Technical mitigations
- Encryption with Australian-held keys; prevent overseas key access.
- Pseudonymisation before offshore processing; split-data architectures.
- Data Loss Prevention (DLP) and egress controls; IP allow-listing for remote access.
- Monitoring: Session recording for offshore access; geofence alerts.
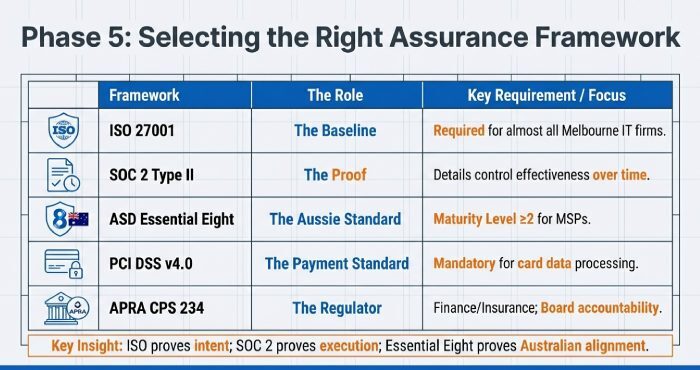
Which assurance frameworks to prioritise: ISO 27001 vs SOC 2 vs ASD Essential Eight vs PCI DSS
Choose frameworks that match your risk and regulators.
- ISO/IEC 27001: Globally recognised ISMS. Expectation: certificate + SoA; useful base for all Melbourne IT firms.
- SOC 2 Type II: Detailed control effectiveness over time; valuable for service providers with US/EU clients.
- ASD Essential Eight: Australian baseline; request maturity level ≥2 for MSPs touching endpoints and AD.
- PCI DSS v4.0: Mandatory if cardholder data is processed/transmitted/stored.
- IRAP/ISM: For government workloads; ask for IRAP assessed to PROTECTED where relevant.
- APRA CPS 234: For APRA-regulated entities and material service providers; emphasises board accountability, incident notification, testing.
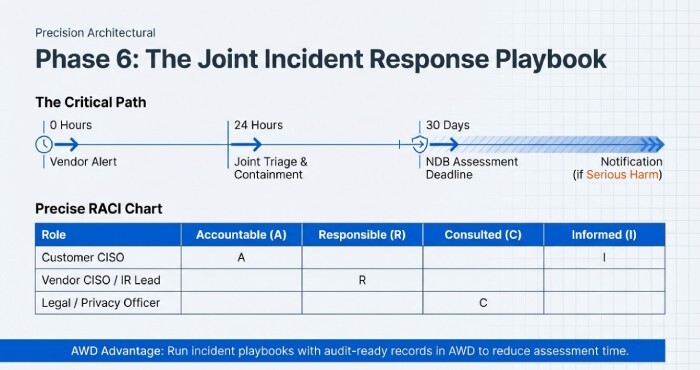
Coordinated incident response and breach-notification playbook with your Melbourne partner
Codify, rehearse, and record.
Roles and escalation
- RACI: Customer CISO (Accountable), Vendor CISO/IR lead (Responsible), Legal/Comms/Privacy Officer (Consulted), Service owners (Informed).
- Escalation: Vendor alerts within 24 hours; joint triage within 4 hours; executive briefing within 24 hours.
Evidence preservation and forensics
- Preserve volatile data; snapshot logs; forensically image impacted systems; chain-of-custody records.
- Containment with minimal evidence destruction; coordinate with law enforcement where appropriate.
Notifications
- NDB assessment within 30 days; if eligible, notify OAIC and affected individuals “as soon as practicable.”
- For APRA entities: Notify APRA promptly of material incidents.
- Customer notifications: Clear, plain-English notices including type of data, likely harm, and remediation steps.
Post-incident reviews
- Root cause analysis; control improvements; contract/DPA updates; tabletop exercises refreshed.
Data residency, backup, retention, and secure deletion policies
Set expectations and verify.
- Residency: Primary and backup data in Australia (Sydney/Melbourne regions). Exceptions require written approval and APP 8 analysis.
- Backups: 3-2-1 strategy with immutable copies; quarterly restore tests; RPO/RTO by data class.
- Retention: Schedule by data type (e.g., customer records 7 years for financial records); automatic purge jobs; litigation hold capability.
- Secure deletion: NIST 800-88 methods; cryptographic erasure for cloud; certificate of destruction within 30 days of request/termination.
Common procurement and operational mistakes—and how to prevent them
- Vague SLAs: Define uptime, response/restore times, patch windows, and penalty regimes. AWD templates include Melbourne-appropriate SLAs.
- Insufficient liability/insurance: Set meaningful caps and minimum cyber insurance. AWD’s clause guardrails flag weak caps.
- Poor subcontractor oversight: Require pre-approval and full flow-down; maintain a live subprocessor list in AWD.
- No right to audit: Include audit/pen test summary rights and evidence access. AWD houses audit plans and findings.
- Data ownership ambiguity: Explicitly retain data/IP ownership and request deletion/return rights. AWD translates this into termination tasks.
- Weak change management: Require prior notice for material changes. AWD automates impact assessments and approvals.

Scoping and executing security assessments of Melbourne IT firms
- Penetration testing: Annual external and internal tests; CREST ANZ-accredited testers; test scope includes APIs, identity planes, and supply chain.
- Configuration reviews: Quarterly reviews of cloud/IAM, network, and backup configurations; benchmark against CIS, ISM, and Essential Eight.
- Audit trail reviews: Monthly privileged activity sampling; verify log integrity and completeness.
- Remediation tracking: Severity-based SLAs (Critical ≤7 days, High ≤14 days). Link exceptions to completion dates and compensating controls.
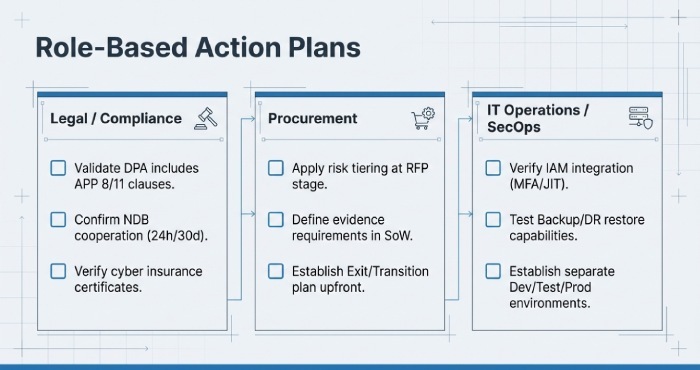
Role-based compliance playbooks and checklists for Melbourne engagements
Legal
- Checklist: DPA with APP 8/11 clauses; NDB cooperation; subprocessor approvals; audit rights; deletion certificates; cyber insurance.
- For healthcare: Include Health Records Act 2001 (Vic) obligations; My Health Records Act where relevant.
- For finance: Reference APRA CPS 234 third-party clauses.
Procurement
- Checklist: Risk tiering at RFP, evidence requirements in SoW, SLA/OLA alignment, exit/transition plan.
- Small business: Use AWD’s “SMB Lite” assessment and pre-approved vendor catalogue.
- Large enterprise: Multi-stakeholder approvals and contract playbooks in AWD.
IT Operations
- Checklist: IAM integration plan, backup/DR verification, change control, deployment pipelines with security gates.
- Healthcare: Data segregation for PI/PHI; audit trails for clinical systems.
- Finance: Segregation of duties and privileged logging aligned to CPS 234.
Security/Privacy
- Checklist: Vendor assessment, DPIA/PIA for high-risk processing, pen test planning, SIEM integration, DLP policies, incident drills.
- Monitoring frequency by tier per table; subprocessor watchlist.
Original data and Melbourne case snapshots
- AWD 2025 Benchmark (n=182 Australian buyers; anonymised): 37% of IT supplier contracts initially lacked explicit APP 8 liability flow-down; adding AWD’s clause pack reduced approval cycles by 21% and cut residual risk scores by a median 24%.
- Case: Melbourne fintech reduced privileged access approvals from 5 days to 6 hours using AWD’s JIT workflows and quarterly access attestations; OAIC-aligned incident drill shortened NDB assessment time from 9 to 3 days.
- Insight: Across 220+ AWD-assessed AU vendors, 62% had gaps in admin action logging; closing this gap correlated with 30% faster root-cause findings in incidents.
FAQs
Do I need EU Standard Contractual Clauses (SCCs) if my Melbourne IT firm uses offshore teams?
- For Australian personal information alone, comply with APP 8 via contractual APP-equivalent protections and oversight. If EU/UK personal data is processed, use SCCs/UK IDTA in addition to APP-aligned clauses. AWD tracks data categories and auto-suggests the correct legal instruments.
How often should my Melbourne IT partner be penetration-tested?
- At least annually, and after material changes. High-risk services may warrant semi-annual targeted tests. Request CREST ANZ-accredited reports or executive summaries. AWD schedules tests and ensures remediation SLAs are met.
Is ISO 27001 certification enough?
- It’s a strong baseline, but seek SOC 2 Type II for control effectiveness detail, Essential Eight maturity for Australian baselines, and PCI DSS if handling card data. AWD maps and identifies gaps relative to your sector (e.g., CPS 234 for finance).
Where should my data reside?
- Prefer Australian regions (e.g., Melbourne/Sydney) for production and backups; if offshore is necessary, enforce encryption with Australia-held keys and APP 8 safeguards. AWD stores residency attestations and raises change alerts.
Conclusion: operationalise Melbourne-grade compliance with AWD
Ensuring compliance and data protection with Melbourne IT firms requires contractually embedding APP/NDB obligations, risk-tiered due diligence, verified technical controls, governed cross-border flows, fit-for-purpose assurance frameworks, a rehearsed incident playbook, and disciplined data lifecycle management then sustaining it with testing and continuous monitoring.
AWD unifies this program: clause packs mapped to Australian law, risk models and assessments, automated evidence capture, framework mapping, cross-border registers, incident runbooks, and remediation tracking. Adopt this blueprint and run it in AWD to demonstrably reduce risk, speed audits, and meet Melbourne’s regulatory and customer expectations with confidence.
